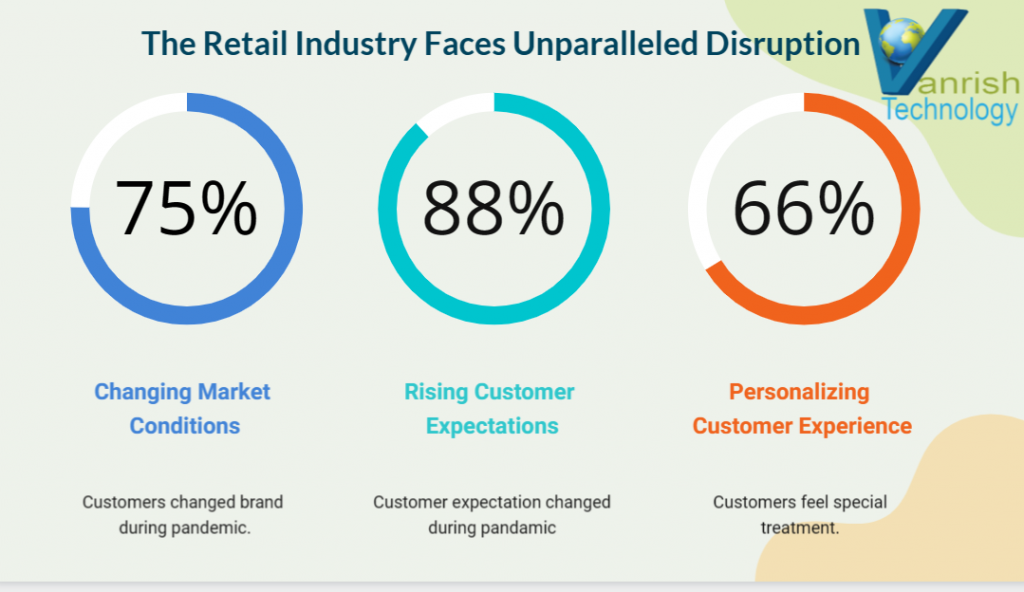
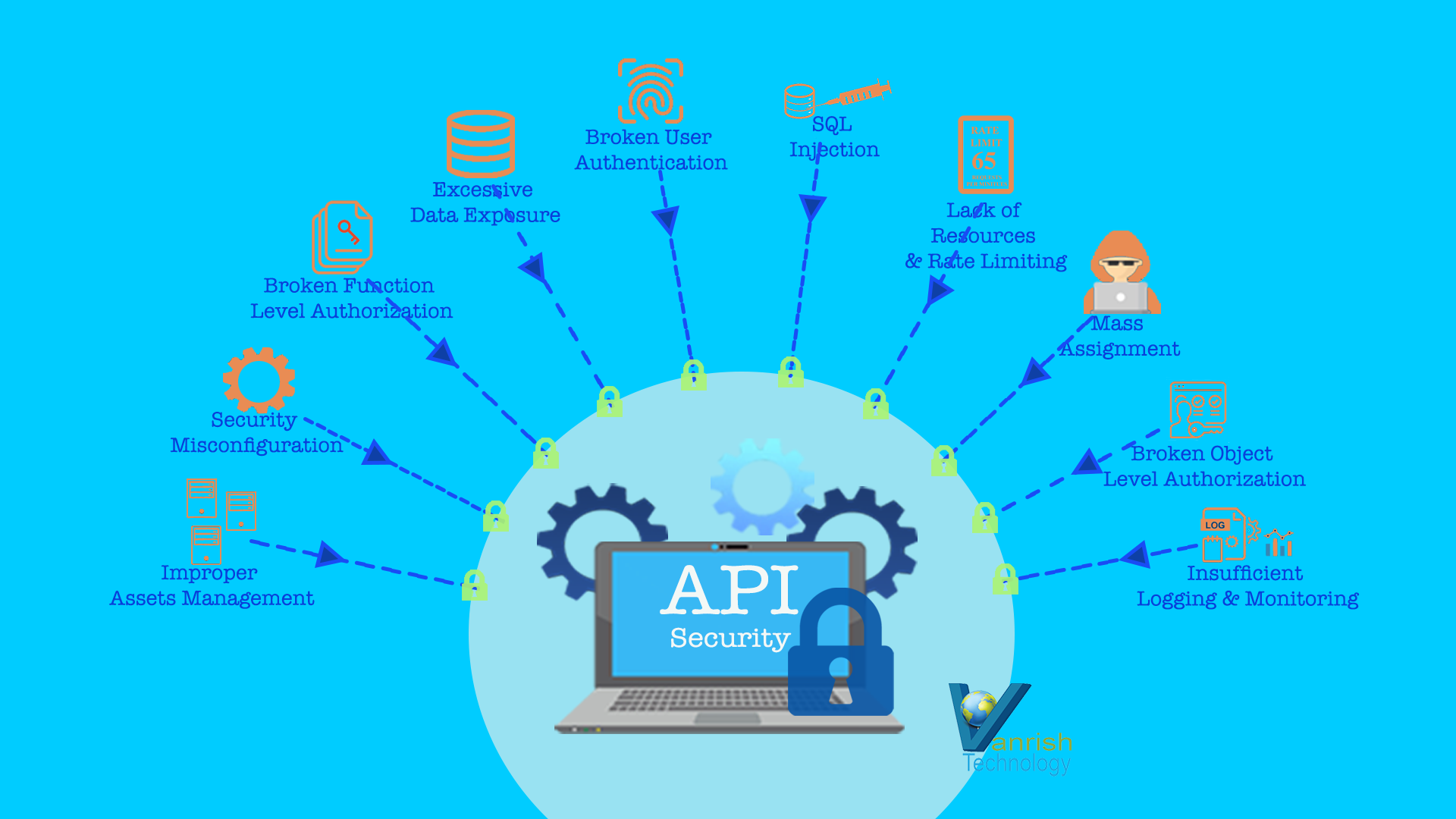
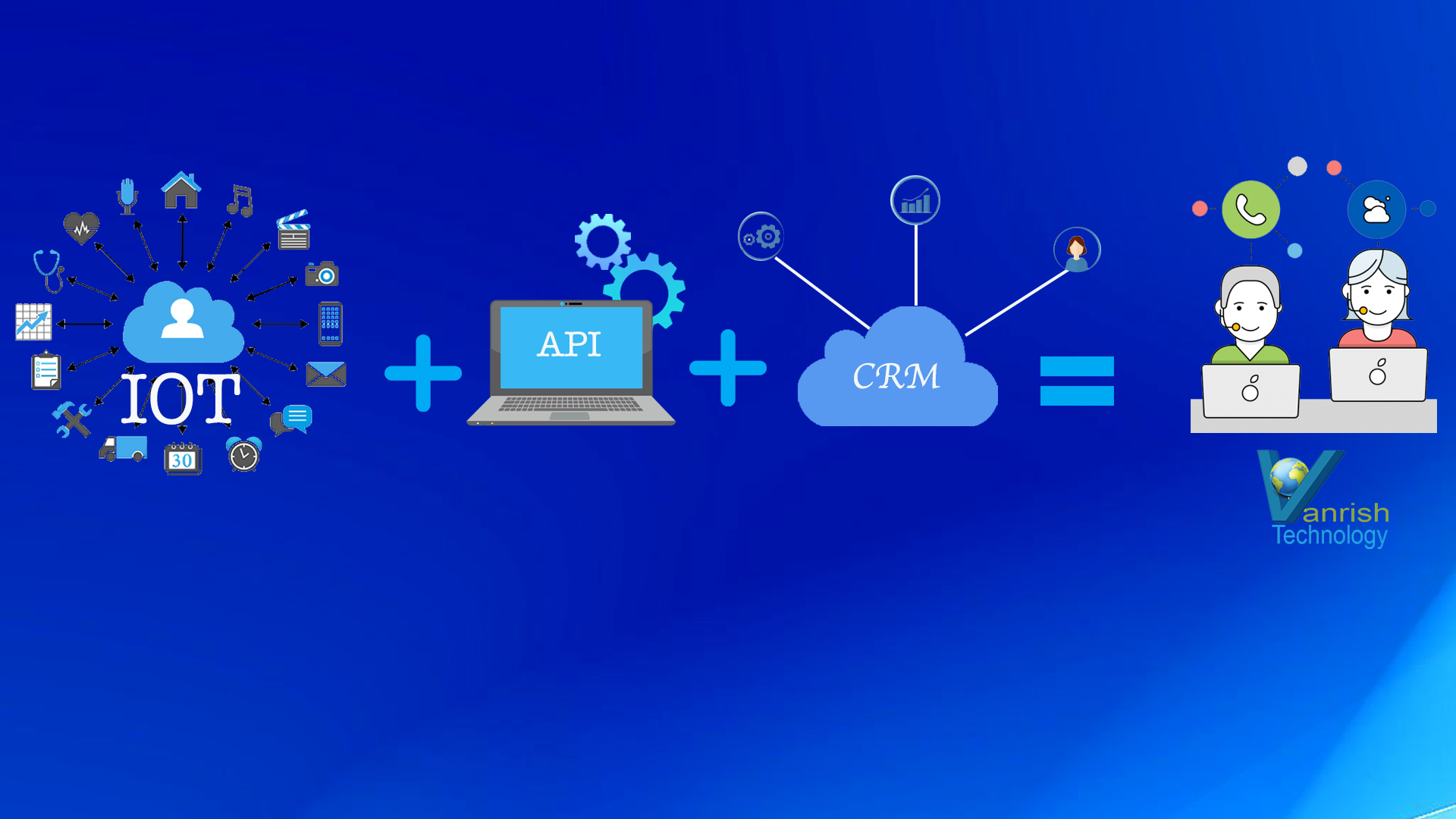
When organization is migrating to digital transformation, data security is a big concern. Digital transformation impacts every aspect of business operation and execution. The volume of data that any organization creates, manipulates, and stores digitally is growing, and that drives a greater need for data governance. Large volume of data security is the biggest challenge for any organization for their entire data lifecycle.
Data security is a process to protect sensitive data from unauthorized access, corruption, or theft during the entire data lifecycle.
Here are a few steps to mitigate data risk and implement data security.
- Event Monitoring
- Data Detection
- Data Encryption
- Data Audit Trail
Event Monitoring – This activity includes Prevention, mitigation, and monitoring threats to sensitive data.
- Monitor user activity – Know who is accessing data from where with real-time event streaming and min 3-6 months of event history.
- Prevent and mitigate threats – Define and build Transaction Security policies using declarative conditions or code to prevent and mitigate threats.
- Drive adoption and performance – Analyze user behavior to enable security training for organization and find security bottlenecks to improve user experience.
- Event Log Files – Create event log file for rich visibility into your org for security, adoption and performance purposes
Data Detection – Find and classify the sensitive data quickly and mitigate data risk.
- Monitor Data Classification Coverage – Determine which data in your organization have been categorized versus uncategorized. High sensitive data needs to be secure properly. Label data appropriately to manage data security.
Data Encryption – Encrypt sensitive data at rest while preserving business functionality.
- Encrypt data and maintain functionality – Protect data and attachments while data search, lookups, transportation and storage.
- Key Management – Data encryption key management is very important to secure organization data. It includes control and authorization of data encryption keys.
- Policy Management – Data policy management is defining and managing rules or procedures for accessing data. It allows individuals to follow certain processes to access data during storing or transit..
Data Audit Trail – It allows strengthening data integrity for an extended period. This strengthening data integrity process enables compliance and gains insights.
- Data History – Store data as long as you can use this historical data for audit Trail or delete if you do not need this data.
- Data retention policy – Data retention policy defines what data or how long this historical data needs to be stored for audit. Based on sensitivity of data you can archive from 3-6 months or more.
- Insight of data – Create insight and dashboard for data audit transparency. It allows any organization to track any compliance or data security issue.
Rajnish Kumar, the CTO of Vanrish Technology, brings over 25 years of experience across various industries and technologies. He has been recognized with the “AI Advocate and MuleSoft Community Influencer Award” from the Salesforce/MuleSoft Community, showcasing his dedication to advancing technology. Rajnish is actively involved as a MuleSoft Mentor/Meetup leader, demonstrating his commitment to sharing knowledge and fostering growth in the tech community.
His passion for innovation shines through in his work, particularly in cutting-edge areas such as APIs, the Internet Of Things (IOT), Artificial Intelligence (AI) ecosystem, and Cybersecurity. Rajnish actively engages with audiences on platforms like Salesforce Dreamforce, World Tour, Podcasts, and other avenues, where he shares his insights and expertise to assist customers on their digital transformation journey.