API is a key component of digital transformation. API is the interface of your legacy and SAAS data. The goal of APIs is to facilitate the transfer and enablement of data between your system and external users. APIs are typically available through public networks like the internet to communicate to external users and expose your data into the public domain.
Since your data is exposed into the public domain through APIs, It can lead to a data breach. APIs can be broken and expose sensitive personal as well as company data. An insecure API can be an easy target for hackers to gain access to your system and network. Rise of IOT devices and usage of APIs by these IOT devices, APIs are now more vulnerable.
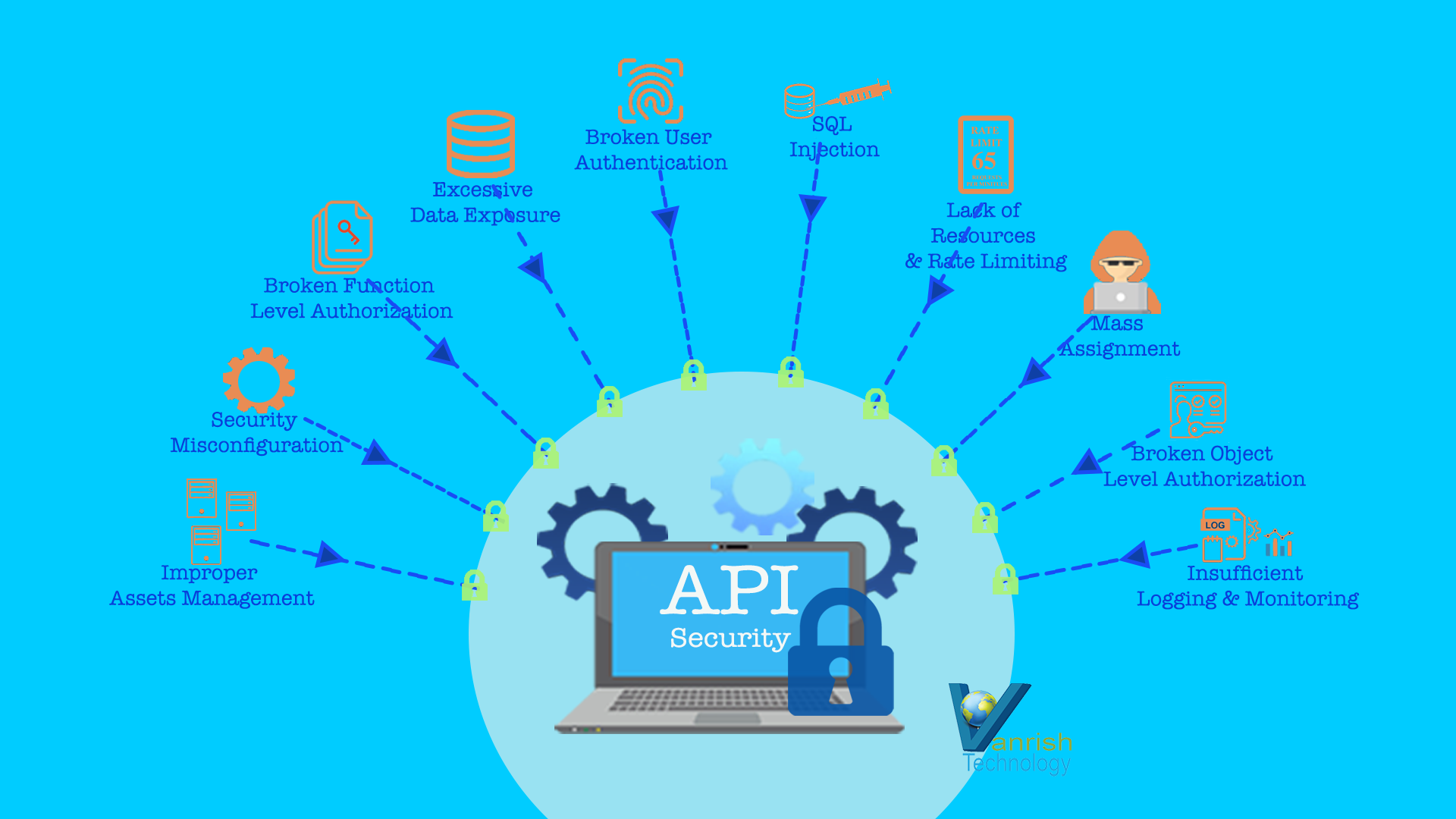
According to owasp, these are 10 main API vulnerabilities.
- Broken Object Level Authorization – Expose endpoints that handle object identifiers, creating a wide attack surface Level Access Control issue.
- Broken User Authentication – Authentication mechanisms are implemented incorrectly.
- Excessive Data Exposure – Developers expose all object properties without considering their individual sensitivity
- Lack of Resources & Rate Limiting – APIs do not impose any restrictions on the size or number of resources that can be requested by the client/user, lead to Denial of Service (DoS) attack on APIs
- Broken Function Level Authorization – Complex access control policies with different hierarchies lead to authorization flaws.
- Mass Assignment – Without proper properties filtering based on an allowlist, usually leads to Mass Assignment.
- Security Misconfiguration – Misconfiguration or lack of Security configuration is commonly a result of insecure APIs
- SQL Injection – SQL Injection occurs when untrusted data is sent to an interpreter as part of a command or query.
- Improper Assets Management – APIs tend to expose more endpoints than traditional web applications lead to improper expose APIs.
- Insufficient Logging & Monitoring – Insufficient logging and monitoring fail to find your vulnerability and broken integration.
How to mitigate API security risk?
- API supports secure sockets layer (SSL), transport layer security (TLS), and Hypertext Transfer Protocol Secure (HTTPS) protocols, which provide security by encrypting data during the transfer process.
- Apply Basic Auth minimum with API or if you want to more secure your API then enable 2 way authentication through OAuth framework .
- Apply Authorization on each API resource to more control on API security through external Identity and access management provider (IAM).
- Use encryption and signatures to all your API exposed personal and organizational sensitive data.
- Apply API throttling through API manager to control number of user access per API (Rate Limiting).
- Implement best practice of exception handling on your APIs to hide all your internal server and database information to mitigate SQL injection security risk.
- Use Service Mesh to manage different layers of API management and control.
- Audit your APIs and remove all unused API from your API catalog.
- Add proper logging, Monitoring and Alerting on your APIs to keep track of your APIs activity.
Conclusion: APIs are a critical part of modern AI, mobile, SaaS, IOT and web applications. APIs Security should be the main focus on strategies and solutions to mitigate the unique vulnerabilities and security risks .
Rajnish Kumar, the CTO of Vanrish Technology, brings over 25 years of experience across various industries and technologies. He has been recognized with the “AI Advocate and MuleSoft Community Influencer Award” from the Salesforce/MuleSoft Community, showcasing his dedication to advancing technology. Rajnish is actively involved as a MuleSoft Mentor/Meetup leader, demonstrating his commitment to sharing knowledge and fostering growth in the tech community.
His passion for innovation shines through in his work, particularly in cutting-edge areas such as APIs, the Internet Of Things (IOT), Artificial Intelligence (AI) ecosystem, and Cybersecurity. Rajnish actively engages with audiences on platforms like Salesforce Dreamforce, World Tour, Podcasts, and other avenues, where he shares his insights and expertise to assist customers on their digital transformation journey.

