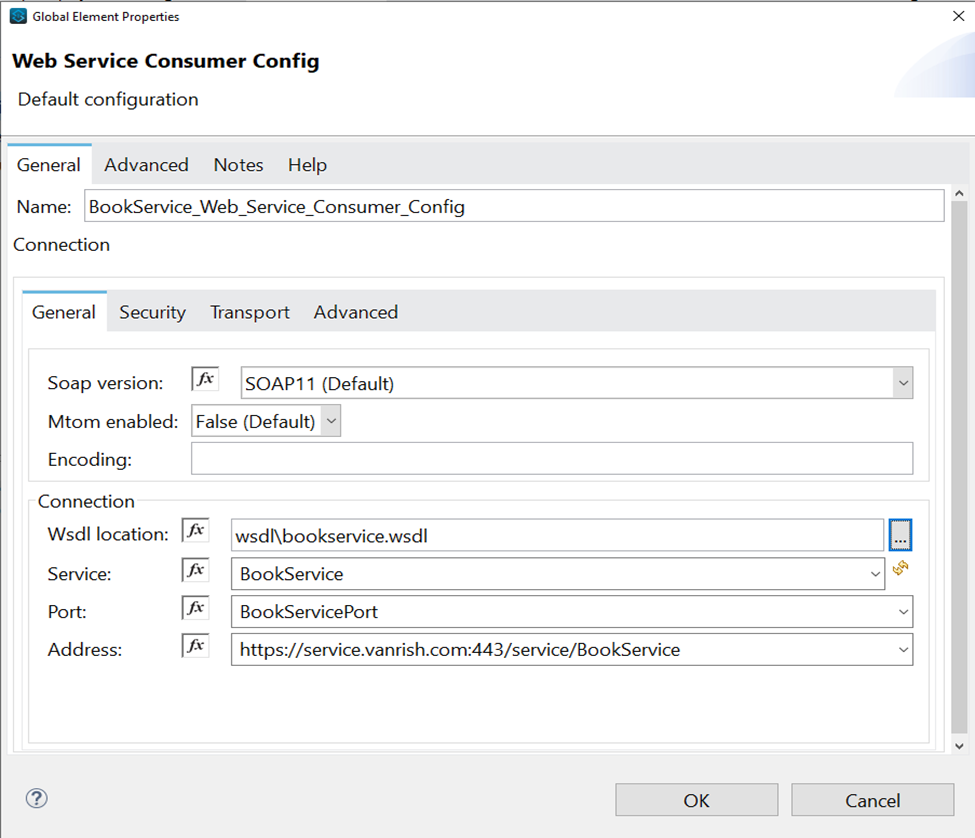
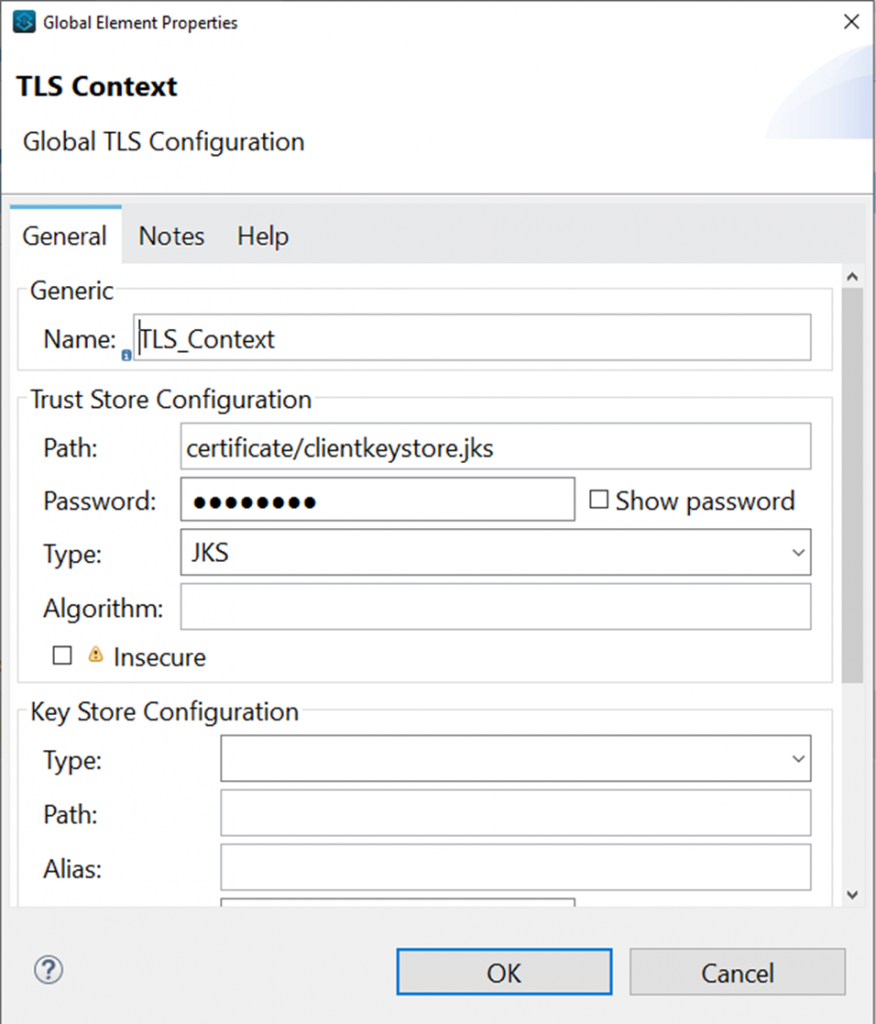
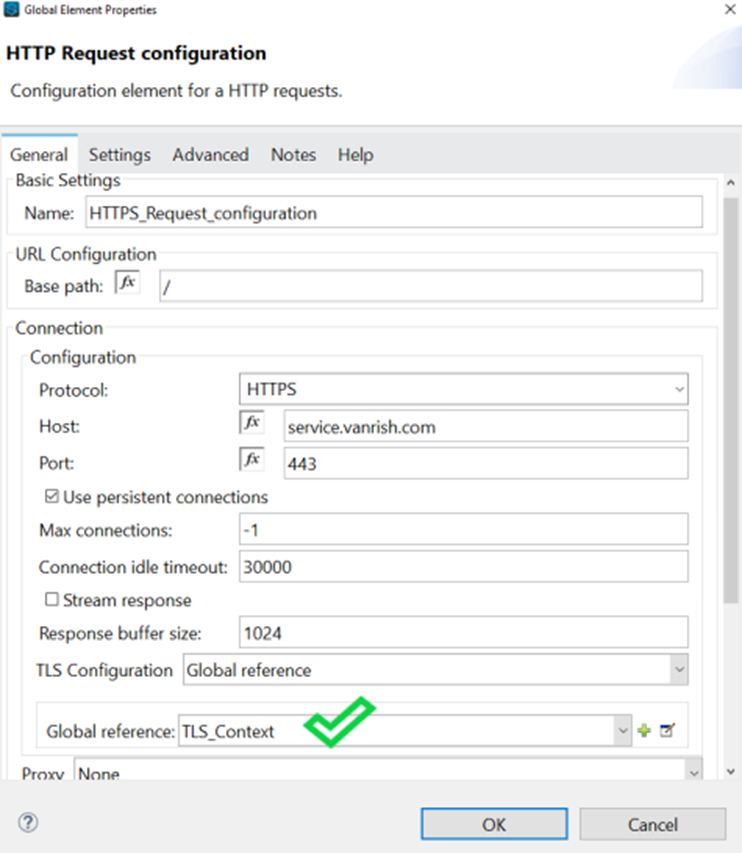
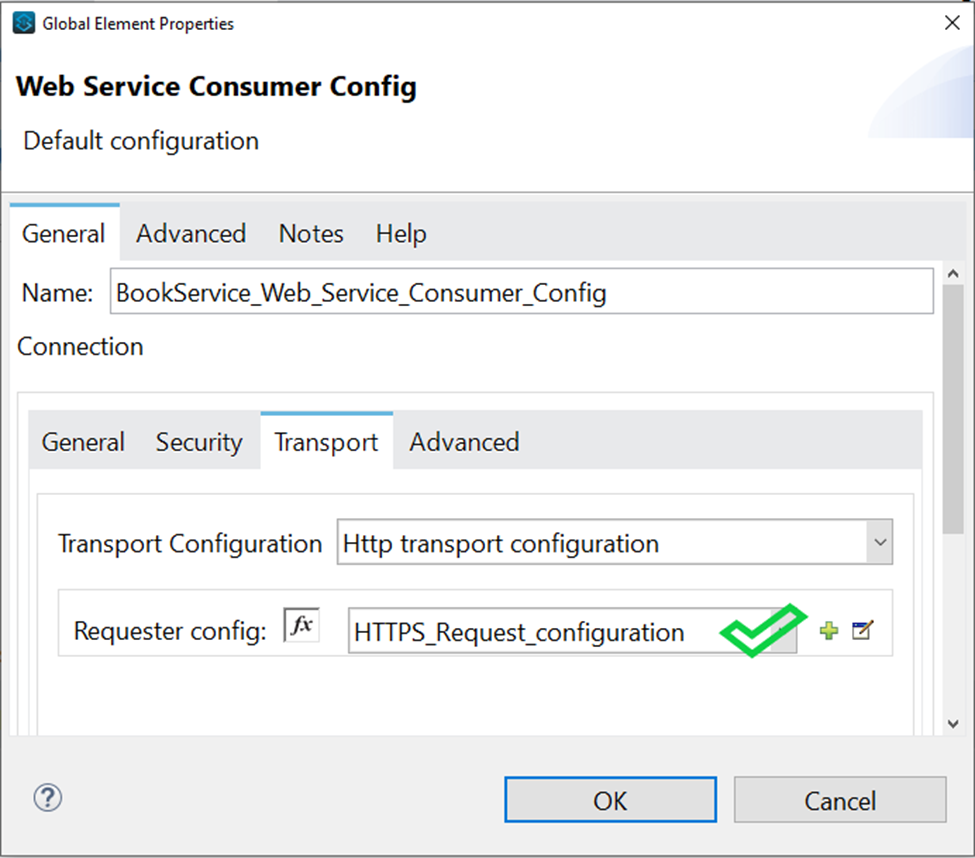
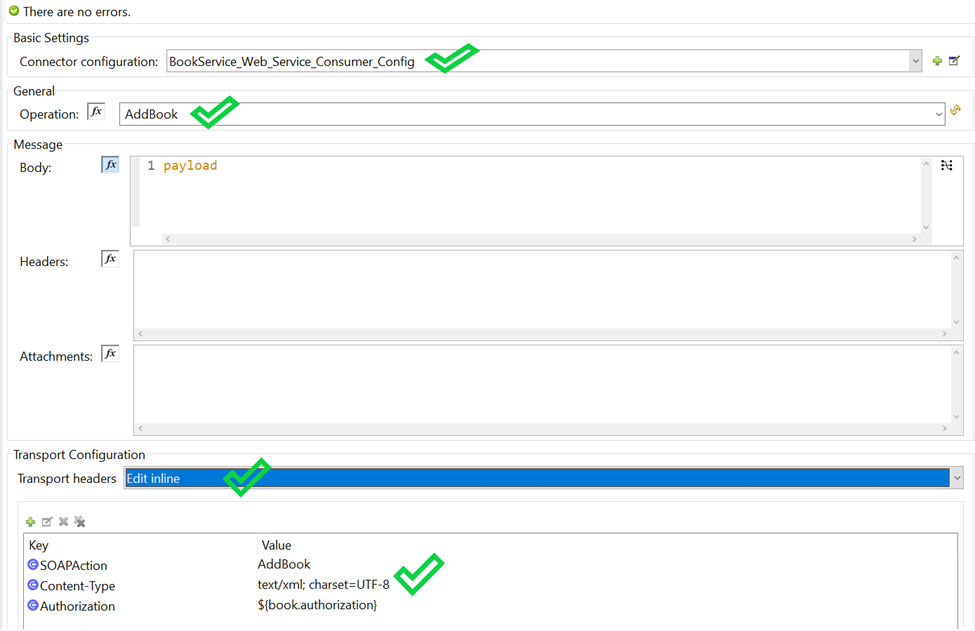
Anypoint Platform acts as a client provider by default, but you can also configure external client providers to authorize client applications. As an API owner, you can apply an OAuth 2.0 policy to authorize client applications that try to access your API. You need an OAuth 2.0 provider to use an OAuth 2.0 policy. You can configure more than one client provider and associate the client providers with different environments. If you configure multiple client providers after you have already created environments, you can associate the new client providers with the environment.
MuleSoft supports client management by identity providers that implement the OpenID Connect Dynamic Client Registration open standard. MuleSoft explicitly verifies support in Anypoint Platform for Salesforce, Okta, and OpenAM v14 Dynamic Client Registration. The following table contains examples of the URLs you need to supply, depending on your provider, during registration.
| URL Name | Okta Example URL | OpenAM Example URL | Salesforce Example URL |
| Base | https://example.okta.com/oauth2/v1 | https://example.com/openam/oauth2 | https://example.salesforce.com/services/oauth2 |
| Client Registration | {BASE URL}/clients | {BASE URL}/connect/register | {BASE URL}/register |
| Authorize | {BASE URL}/authorize | {BASE URL}/authorize | {BASE URL}/authorize |
| Token | {BASE URL}/token | {BASE URL}/access_token | {BASE URL}/token |
| Token Introspection | {BASE URL}/introspect | {BASE URL}/introspect | {BASE URL}/introspect |
| URL Name | Okta Example URL | OpenAM Example URL | Salesforce Example URL |
Steps to Create External Client Provider
- Log in to Anypoint Platform using an account that has the organization administrator role.
- In Anypoint Platform, click Access Management.
- In the menu on the left, click Client Providers.
- Click Add Client Provider, and then select OpenID Connect Dynamic Client Registration.
The Add OIDC client provider page appears.
- After obtaining values from your identity provider’s configuration, complete the following required fields in each section:
- Dynamic Client Registration
- Issuer: URL that the OpenID provider asserts is its trusted issuer.
- Client Registration URL: The URL to dynamically register client applications as a client application for your identity provider.
- Authorization Header
- For Okta, this value is SSWS ${api_token}, where api_token is an API token created through Okta.
- For ForgeRock, this value is Bearer ${api_token}, where api_token is an API token created through ForgeRock.
- For Salesforce, this value is Bearer ${api_token}, where api_token is an API token created through Salesforce. In Advanced Settings you can also select:
- Disable server certificate validation: Disables server certificate validation if your OpenID client management instance presents a self-signed certificate, or one signed by an internal certificate authority.
- Enable client deletion in Anypoint Platform: Enables deletion of clients created with this integration.
- Enable client deletion and updates in IdP: To use this option, you must also select the Enable client deletion in Anypoint Platform option.
- Token Introspection Client
- Client ID: The client ID for an existing client in your IdP capable of introspection of all tokens from all clients.
- For Okta, this value should be a “Confidential” client.
- For ForgeRock, this value should be a “Confidential” client.
- For Salesforce, this value should be a “Confidential” client.
- Client Secret: The client secret that corresponds to the client ID.
- Client ID: The client ID for an existing client in your IdP capable of introspection of all tokens from all clients.
- OpenID Connect Authorization URLs
- Authorize URL: The URL where the user authenticates and grants OpenID Connect client applications access to the user’s identity.
- Token URL: The URL that provides the user’s identity, encoded in a secure JSON Web Token.
- Token Introspection URL: endpoint that returns metadata about the access token, including expiration and token active state.
- Dynamic Client Registration
Rajnish Kumar, the CTO of Vanrish Technology, brings over 25 years of experience across various industries and technologies. He has been recognized with the “AI Advocate and MuleSoft Community Influencer Award” from the Salesforce/MuleSoft Community, showcasing his dedication to advancing technology. Rajnish is actively involved as a MuleSoft Mentor/Meetup leader, demonstrating his commitment to sharing knowledge and fostering growth in the tech community.
His passion for innovation shines through in his work, particularly in cutting-edge areas such as APIs, the Internet Of Things (IOT), Artificial Intelligence (AI) ecosystem, and Cybersecurity. Rajnish actively engages with audiences on platforms like Salesforce Dreamforce, World Tour, Podcasts, and other avenues, where he shares his insights and expertise to assist customers on their digital transformation journey.